The ARCADIAN-IoT framework integrates a comprehensive approach towards managing privacy, security, identity, trust, and recovery within IoT systems through its specialised components distributed across several planes.
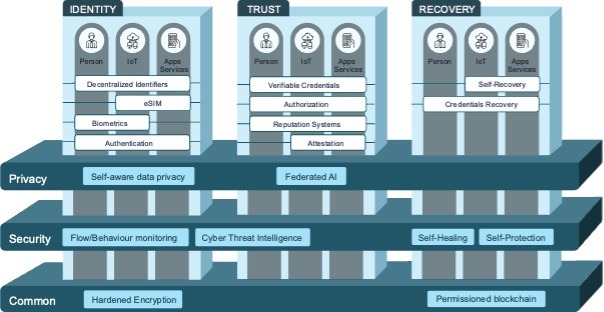
This structure embodies a holistic view of IoT security and privacy, emphasizing decentralized management, data protection, and recovery capabilities to ensure comprehensive protection and trust across IoT systems.
Privacy Plane
Empowers users with the Self-aware Data Privacy and Federated AI components to control data privacy through user-defined policies and leverage federated learning for privacy-preserving, decentralized artificial intelligence.
The Self-aware Data Privacy (SADP) component introduces an innovative approach to managing and safeguarding data privacy in IoT settings. This system empowers users with the tools to actively define and enforce their privacy preferences through sophisticated policy management. It utilizes cutting-edge modules for enforcing attribute-based data encryption or anonymization and suggests privacy policies based on user-defined criteria and similar data scenarios. By integrating advanced technologies like Open Policy Agent (OPA) for decision-making and Envoy Proxy for policy enforcement, SADP enhances user control over data privacy. This solution represents a significant leap in ensuring consistent and user-centric data privacy across various services, underscoring ARCADIAN-IoT’s commitment to advanced, flexible, and user-friendly privacy management mechanisms.
The Federated AI component introduces significant advancements in privacy-preserving machine learning by optimizing Federated Learning (FL) for IoT contexts. This innovation enhances security and efficiency in distributed learning across devices without centralizing sensitive data, maintaining privacy. It addresses the challenge of data heterogeneity and ensures learning accuracy and robustness against malicious activities. Innovations include techniques for rebalancing diverse data and resizing models to improve communication efficiency and protect against adversarial attacks. By open-sourcing developed code, ARCADIAN-IoT fosters community research and application, demonstrating a commitment to improving federated learning technologies for real-world IoT applications while ensuring data privacy and model integrity, embodying EU’s AI Act principles.
Security Plane
The Network Flow Monitoring component delivers significant advancements in network security for IoT and 5G infrastructures. This innovation extends the capabilities of network intrusion detection systems to comprehensively identify DDoS attacks across the entire 5G network. By integrating with existing systems like Snort and supporting a broad range of networks—including traditional IP, overlay, and mobile operator networks—the component combines versatility and coverage. Its dual subcomponent architecture features also a specialized Security Flow Monitoring Agent, enhances detection granularity and effectiveness. Additionally, its extended North Bound Interface facilitates detailed attack analysis, aiding in swift mitigation actions. This component not only elevates the security posture of diverse network environments but also ensures robust protection against an array of cyber threats, marking a crucial step forward in safeguarding 5G and IoT ecosystems.
The Device Behaviour Monitoring component marks a significant advancement in IoT device security, focusing on detecting anomalous behaviour as an indicator of potential security breaches or malfunctions. Acting as a host-based intrusion detection system, this component scrutinizes device-specific events, such as system calls and authentication attempts, for anomalies. It utilizes machine learning models enhanced through federated learning for ensuring data privacy while improving model accuracy. The integration of real-time anomaly detection with the classification of events provides immediate insights into device operations, enhancing the system’s responsiveness to potential threats. The inclusion of explainable AI techniques further enriches the component, offering transparency into the decision-making process of the models. This innovation enhances the security framework for IoT devices and underscores the ARCADIAN-IoT project’s commitment to advancing IoT security through cutting-edge technological research and development.
The Cyber Threat Intelligence (CTI) component significantly advances IoT security by focusing on the collection, analysis, and dissemination of cyber threat data. It employs the Malware Information Sharing Platform (MISP) and tailors it for IoT, enabling efficient threat data handling, and sharing in a privacy-conscious manner. Innovatively, it integrates with Federated AI for privacy-preserving sharing of Indicators of Compromise (IoCs) among IoT devices. Introducing novel TinySTIX and TinyTAXII formats for lightweight CTI data exchange and machine learning for IoC processing, it offers a comprehensive approach to managing cyber threats. The component’s design includes mechanisms for parsing, ranking, classifying, and clustering threat data, enhancing IoT devices’ ability to detect and respond to security incidents more intelligently. Demonstrating high performance in threat intelligence tasks, this component marks a forward leap in protecting the IoT ecosystem from complex cyber threats, highlighting ARCADIAN-IoT’s commitment to pioneering IoT security innovations.
The Network Self-Protection component in the ARCADIAN-IoT project is a pioneering advancement in IoT security, focusing on defending network infrastructure and IoT devices from volumetric DDoS attacks. Leveraging OpenVSwitch for enhanced programmability and security policy enforcement, it operates collaboratively with the Network Flow Monitoring and Network Self-healing components for a comprehensive attack detection and mitigation strategy. Innovations include a traffic classifier for managing nested network traffic in 4G/5G IoT networks, OpenFlow protocol extension for data plane flexibility, and OVS Netlink API extension supporting large-scale IoT device management. These advancements ensure robust, scalable, and autonomous network protection, marking a significant leap in IoT security solutions.
The ARCADIAN-IoT’s Device Self-Protection component enhances IoT security by automating the enforcement of protection policies directly on devices. It mitigates threats identified by the framework (e.g. Device Behaviour Monitoring and Cyber Threat Intelligence) with minimal human intervention, allowing devices to autonomously respond to threats (e.g. disabling certain network protocols or restricting access to sensitive areas) based on dynamic policy application. The awareness to information from various and rich sources, including detected anomalies and reputation scores, guides policy creation and enforcement, ensuring a robust defense mechanism against evolving cyber threats. This component represents a significant step forward in IoT device security, leveraging the collective intelligence of the ARCADIAN-IoT framework to proactively protect heterogeneous devices.
The Network Self-healing component is a significant advancement aimed at fortifying IoT networks against cyber threats, especially where conventional defence mechanisms fall short. By smartly pinpointing both the actions needed to counteract an assault – like redirecting or blocking traffic – and the network’s strategic points for these actions, it leverages a sophisticated understanding of network topology. This component seamlessly collaborates with the Network Flow Monitoring tool for enriching its insights with detailed recovery instructions. With capabilities to handle complex network structures, including 4G/5G IoT setups, it introduces dynamic, distributed policy enforcement for more effective, automated attack mitigation. This significant innovation reduces manual intervention, steering towards more autonomous network management and illustrating a robust approach to safeguarding IoT infrastructures.
Common Plane
The Hardened Encryption with SIM as Root of Trust introduces an innovative approach to securing and authenticating private IoT data through advanced cryptographic mechanisms. This component employs a decentralized Attribute-Based Encryption (ABE) paradigm, leveraging the Subscriber Identity Module (SIM) as a hardware-based Root of Trust (RoT) for enhanced security. The integration of SIM technology enables digital signing of encrypted payloads, providing guarantees about data authenticity without exposing cryptographic keys. Additionally, the system features a decentralized key management system for distributing ABE keys and access rights, reducing the risk of single points of failure. The ABE paradigm allows for flexible encryption and authentication policies, catering to various scenarios without complicating encryption or increasing ciphertext sizes. The component is implemented via a software library supporting diverse devices and programming languages, enabling efficient and secure ABE implementations designed to balance security with performance for IoT devices.
The Hardened Encryption with cryptochip as Root of Trust introduces a specialized encryption system designed for industrial scenarios where IoT devices have very limited capabilities (e.g. microcontroller-powered devices). This system incorporates crypto chips, either as add-on modules or embedded within IoT devices, enhancing the devices’ master firmware with an agent capable of managing encryption keys. It integrates with IoT middleware software platforms tailored for specific scenarios, offering key management for crypto chips, management of ARCADIAN-IoT integrated security systems as endpoints, a decentralized authorization agent, and interfaces for integration with third-party platforms through APIs and message bus (i.e. RabbitMQ). Key innovations include the development of industrial IoT device motherboards accommodating crypto chips, extension boards for data gathering and remote commands, a comprehensive hardware testing environment, a master firmware system with a command-line interface tool, and modular, Docker-contained middleware components capable of integrating with ARCADIAN-IoT’s security systems and rapid API and RabbitMQ interfacing with external IoT platforms.
The Permissioned Blockchain component serves as a foundational element, providing immutable auditability and traceability for ARCADIAN-IoT operations or data (e.g. public Decentralized Identifiers, cryptographic keys for Hardened Encryption, updated reputation scores). This approach employs a private, permissioned blockchain methodology, where participation and transaction permissions are restricted to ensure data security and integrity. Key innovations include the permissioned structure for controlled access, high throughput and enterprise focus, integration with smart contracts and decentralized applications (dApps), decentralized and transparent operations without a central authority, and mechanisms for ensuring privacy and security. The blockchain network is built on Hyperledger Fabric 2.5, known for its modular architecture, performance, and support for privacy-oriented features. It comprises multiple peer nodes for fault tolerance and data integrity, with tailored smart contracts facilitating secure publication and verification of ARCADIAN-IoT data objects. This component is integral to several ARCADIAN-IoT applications, ensuring secure data exchange, identity verification, and the execution of encrypted transactions, while paving the way for future enhancements in identity management and IoT security solutions.
Identity Plane
The Network Flow Monitoring component delivers significant advancements in network security for IoT and 5G infrastructures. This innovation extends the capabilities of network intrusion detection systems to comprehensively identify DDoS attacks across the entire 5G network. By integrating with existing systems like Snort and supporting a broad range of networks—including traditional IP, overlay, and mobile operator networks—the component combines versatility and coverage. Its dual subcomponent architecture features also a specialized Security Flow Monitoring Agent, enhances detection granularity and effectiveness. Additionally, its extended North Bound Interface facilitates detailed attack analysis, aiding in swift mitigation actions. This component not only elevates the security posture of diverse network environments but also ensures robust protection against an array of cyber threats, marking a crucial step forward in safeguarding 5G and IoT ecosystems.
The eSIM – Hardware-based identification and authentication explores the benefits from moving from traditional SIM technology into its embedded format (eSIM), which retains the security aspects of conventional SIM cards while introducing new capabilities such as remote provisioning and management. The eSIM technology, which eliminates threats related to swapping secure elements between devices due to its embedded nature. Is integrated into the ARCADIAN-IoT project by playing a multifaceted role, acting as a secure connectivity enabler, a secure element for storing critical identity and authentication credentials, a root of trust for encryption and attestation processes, and a local authorization agent capable of self-protection and recovery actions. eSIMs contribute to ARCADIAN-IoT’s multi-factor authentication process, securely storing credentials at the hardware level and leveraging cellular network authentication to authenticate devices and individuals to third-party services without additional credential provisioning, promoting scalability and security. The project aims to demonstrate the innovative usage of this technology while reaching relevant Technology Readiness Level (TRLs), by demonstrating its application across various IoT domains with diverse device characteristics, making the network-based authentication process device and protocol agnostic – underscoring the innovative and adaptive nature of the eSIM technology within the ARCADIAN-IoT framework.
The Biometrics component provides an additional authentication factor for person identification, by enabling person verification based on facial characteristics. This system is designed to work in two main scenarios: verifying individuals using smartphone cameras and through video feeds from drones. Key innovations include developing algorithms for face detection and verification that perform well even in challenging conditions such as varying angles, low resolution, and disturbances typical of UAV operations. Relevant achievements include the creation of a unique dataset and algorithms tailored for drone-based identification, leveraging advanced machine learning frameworks for efficient real-time processing. The system scalability and maintaining high accuracy and reliability of the machine learning models have been identified as promising future research directions.
Trust Plane
The Network-based Authorization component focuses on trust-based authorization enforcement in cellular networks and the secure distribution of trustworthiness information to devices’ secure elements. Key innovations include the dynamic enforcement of network-based authorization, real-time application of authorization policies, and secure distribution of trust information for self-protection and self-recovery actions. Noteworthy achievements include the development and integration of a cellular core network testbed, successful demonstration of technology in IoT scenarios, and a secure mechanism for distributing authorization information to devices.
The Reputation System introduces several innovations, including the use of diverse reputation models (alpha-beta model, alpha-beta with severity, dominance relationships) to assess entities’ trustworthiness within the IoT framework. It addresses GDPR compliance by integrating privacy-focused mechanisms and leverages scalable stream processing technologies for real-time data handling. The system supports distributed and reliable storage of reputation scores and employs a policy-based approach for authorization and attestation according to IoT service providers requirements and policies, jointly enhancing IoT trust, security and privacy management. Further, it incorporates visualization tools to improve transparency and understanding of reputation behaviour.
The Remote Attestation (RA2IoT) framework within ARCADIAN-IoT innovatively addresses IoT security by leveraging Secure Elements like eSIM or crypto chips as a Root of Trust. This approach uniquely supports a broad spectrum of IoT devices, from constrained to less constrained ones, enhancing their trustworthiness. Key innovations include aligning with IETF RATS guidelines for challenge-response mechanisms, adopting CBOR for efficient data serialization, and feeding entities (IoT devices or services) trust modelling solutions (i.e. Reputation System). Additionally, RA2IoT explores novel AI-based remote integrity assessment methods for claim measurement processes, significantly contributing to secure and trustworthy IoT ecosystems.
Recovery Plane
The ARCADIAN-IoT project introduces a comprehensive credential recovery mechanism designed to secure and recover credentials for both personal devices and IoT devices. It utilizes Self-Sovereign Identity (SSI) and SIM-based Network Identity frameworks to ensure the secure management of credentials. Automated processes, coupled with secure backup servers and encryption techniques, enable the recovery of credentials in cases of loss, compromise, or corruption. Noteworthy innovations include encrypted backup storage, selective decryption based on user roles, and automatic credential recovery triggered by reputation score improvements or manual initiation by administrators. These advancements ensure the resilience and trustworthiness of device operations within the ARCADIAN-IoT ecosystem.

